(..continuation from Update #1)
After probably being limited to the restrictive functionality of the ‘Man-on-the-Side (MoTS)’ strategy, the spying agencies would now need to deploy something more to intercept the traffic and not sit on the side to watch

Man-in-the-Middle (MiTM)
This involves by allowing the spying agency to sit ‘in-between’ your device and the internet, often within ISP server infrastructures to intercept, alter, or even redirect your internet traffic, a common practice in many countries
URL Filtering & Blocking
Were aware that these URL Filtering servers have been deployed since 2006 where the PTA can actively look at the URL address you type in & depending on their Whitelist or Blacklist, choose to block your access to the particular domain, more recently there was much hype about Govt of Pakistan acquiring the Great Firewall of China
But keep in mind China controls everything in the mainland, they don’t depend on international companies providing them with essential internet services. For them any international domain for ex Google if they don’t comply with the security demands as instructed by them, the company is totally blocked from the people of China. As an alternate, they have created a huge echo system of alternate apps & websites like Baidu which then supplements the needs of the people and similarly WeChat is the alternate to WhatsApp.
China has total access to encryption keys within these apps, enabling them backdoor access to do deep packet inspection on any traffic from China
Deep Packet Inspection (http & https)
Spying on each packet of information traversing the internet in real-time is a very daunting task, specially if you are doing it on the entire countries internet backbone, but with advance software that they can purchase, DPI is very much possible.
DPI on unencrypted (http) traffic is easy, but with the ever increasing pressure on privacy & security across the world more and more website have implemented encryption (https) across all their portals.
This puts the PTA in a pickle, as they are now unable to decipher encrypted content, specially WhatsApp, hence the then need to install malicious spy software on every device

Installing Malware / Spyware
The cheaters guide to espionage, is to sneak a malicious software into millions of devices which then will give them full access to read every content. To do this on each device is impossible, so they have to find black-hat software to help them
1-CLICK Spyware
These are suspicions links sent as Click Bait to a person hoping that the victim (you) might accidentally click, leading you to a malicious website which quickly installs a small piece of code enabling them to create a loophole into your phone – Such a strategy has been documented by Amnesty to have been used on journalists Vietnam in 2021
1-Click is entirely dependent on YOU, to click, so its usually still considered a ‘hit & a miss’, as many people these days are very cautious about clicking suspicious inks — so this strategy might not be proving them to provide the essential results aka WhatsApp Chats
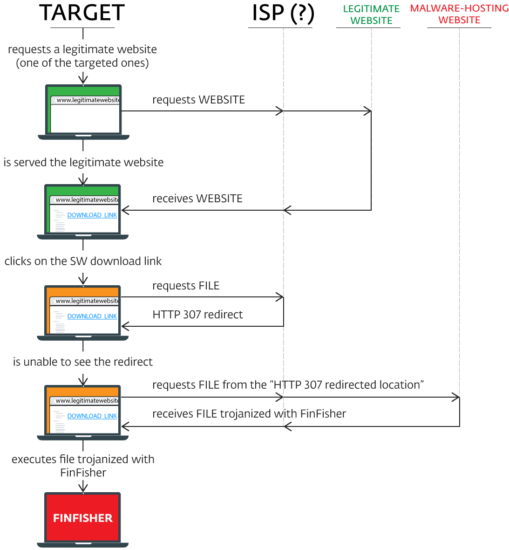
ZERO-CLICK Spyware
The next strategy is to install by some trickery a spyware with absolutely no user/victim interaction and do it automatically — also known as a ZERO-CLICK. By some mysterious ways your device accidentally browses through to a website which installs a spyware without you having ever clicked anything – this is the trickery we need to expose.
This is also where I suspect the recent TELECOM NETWORK INJECTION is happening in Pakistan

—
(... to be continued on to update #3 due to the length of this discussion, this thread discussion is broken into multiple tweets over the next few days)

Comments
One response to “Predator Spyware Installed in Pakistan #2”