Last week’s cellular network disruptions in Pakistan might be linked to the PTA’s acquisition of more advanced ad-on modules from Intellexa (an Israeli-based firm), potentially further enhancing the capabilities of PREDATOR spyware already being used in Pakistan

Internet Throttling Across Pakistan?
A week ago, internet users in Pakistan experienced drastically reduced internet speeds, especially while connecting thru the telecom networks. There was a total silence from governmental sources, acting oblivious to any firewall or internet speed reduction.
But this disruption needed a deeper investigation.
Why Should You Worry?
🇵🇰Peaceful, law-abiding Pakistanis generally have nothing to fear, but this escalation in surveillance capabilities allows the government to invade each persons personal privacy, unfettered access to private messages, photos, and personal data and potentially using it for blackmail.
Understanding their Tactics Helps:
Here’s what I’ve pieced together (this discussion will span multiple threads over the next few days):
MOTIVE: Not Counter Terrorism, but only Anti-Imran Khan Strategy:
Over the last many months, with the entire establishment up in arms against Imran Khan. There’s been a noticeable increase in efforts to counter any pro-Imran Khan/PTI narratives, revealing their breadcrumbs to their espionage strategy – non of these have anything to do with counter-terrorism in Pakistan
The Government’s Espionage Tactics:

My Analysis: Observing PTA’s suspicious activities, it perfectly matches the evidence exposed by Amnesty International in October 2023 in the form of Predator Leaks, reading the supporting documents in the leak one can slowly see the breadcrumb trail of the Predator firewall being gradually deployed for espionage on Pakistanis.
It is my analysis that spy agencies of Pakistan have long since acquired the Predator software (also reported in the leak)
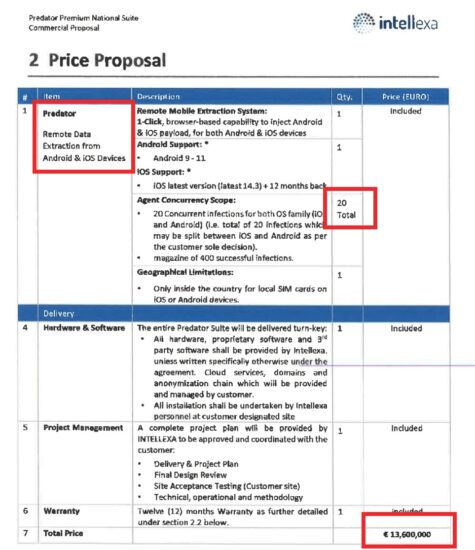
NYT also shared a leaked a Intellexia / Predator company proposal to a client asking for € 13 Million for using this software ONLY ON 20 DEVICES, so its as much of a guess as it might be yours, a country-level deployment can easily run upwards of €100’s of millions
Spyware Deployment Strategy: Espionage on the Internet is multi faceted, could be from the basic physical hacking of the device (not my discussion now) OR latching into the internet backbone to deploy malware & listen to everything that is being done – but Two Basic Espionage Vectors are used:
- Man-on-the-Side (MoTS)
- Man-in-the-Middle (MiTM)
Understanding Man-on-the-Side (MoTS):
As the term suggests, it’s an espionage strategy where the spying agency quietly observes all data flowing through Pakistan, copying it onto their server farms for deep packet inspection. However, with most traffic moving towards https & encrypted is largely unreadable.
PTA has been copying data onto their servers for some time, but there are credible reports suggesting they’ve more recently centralized these operations into one centralized server farm.
Analyzing Unencrypted data is straightforward, but deciphering encrypted data (like WhatsApp’s end-to-end encryption) is extremely challenging, requiring a more direct approach.
(… to be continued due to the length of this discussion, this thread discussion is broken into multiple posts over the next few days)